2. Symmetric Encryption Key
The word 'symmetric' is used because the same key is used for both encryption and decryption.
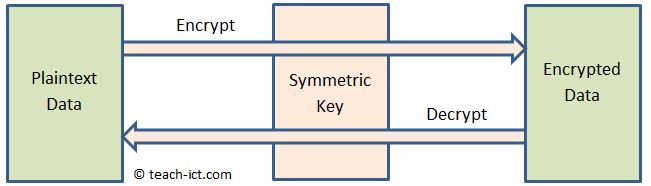
The symmetric key must be kept secret by legitimate systems using it.
A symmetric digital key must be long enough that it becomes infeasible for a normal sized computer to crack the encrypted message in a reasonable amount of time.
The strength of the key is determined by its bit length. For example a 128 bit symmetric key would take a maximum of $2^{128}$ brute force attempts to guess it. At the moment 128 bits is a good balance between privacy for day-to-day use and the processing overhead needed to do the encrypt and decrypt.
An example of a digital symmetric key algorithm is AES-256 (short for Advanced Encryption Standard - 256 bits), and is the standard algorithm used by national governments and commercial organisations for really sensitive information.
Caesar cipher
People have been using non-digital symmetric keys for at least two thousand years. One of the earliest known ciphers is the Caesar cipher, used by the Roman Emperor Julius Caesar for his correspondence. The cipher was very simple - take each letter in the message and swap it for another letter an agreed number of positions up the alphabet. For example if the rule is 3 shifts, A becomes D, B becomes E and so on. It is trivial for a computer to crack this code, but for centuries it was quite good.

Book cipher
You have probably seen this used in wartime spy movies. Agent A and Agent B agree to use a certain book, the huge 'War and Peace' book maybe. Then the message is created by referencing a letter or word in various pages within the book.
For example the code might be 434. Meaning use the 34th letter on page 4.
The whole scheme relies on no-one knowing which book is being used.
Challenge see if you can find out one extra fact on this topic that we haven't already told you
Click on this link: What is a symmetric encryption
